Chapter 19 Technology in Business
Learning Objectives
- Discuss how information technology has transformed business and managerial decision-making.
- Explain why computer networks are an important part of today’s information technology systems.
- Describe the types of systems that make up a typical company’s management information system.
- Explain how technology management and planning help companies optimize their information technology systems.
- Describe the best ways to protect computers and the information they contain.
- Explore and understand the leading trends in information technology.
- Understand the importance and role of cyber security and the impact on companies and personal information if not practiced.
Exploring Business Careers: John Daly, Daly Investment Management, LLC
When meeting with a Daly Investment[1] financial consultant, most likely you are thinking about money, your money. Whether you seek a short-term investment or a retirement nest egg, money will be your focus. You probably will not be thinking about the technological infrastructure required to transmit information throughout a multibillion dollar, nationwide institution such as TD Ameritrade—information that often is private and financial in nature. Luckily for you, however, the company is led by financial advisor John Daly, who works with TD Ameritrade to support his company’s technology needs.
After successful careers at Charles Schwab and Morgan Stanley, Daly knew when he started his own firm he would need IT support so that he could ensure the security of the funds he managed for his customers while focusing on the financial aspects of managing their finances. In addition to providing a financial trading platform for individual investors, TD Ameritrade has a robust set of software as a service (SaaS) cloud-based tools that allow Daly to focus on his core competencies rather than having to hire, train, and maintain a complex set of IT resources that his clients can trust.
Given the size of the assets it manages, TD Ameritrade’s management information system (MIS) is necessarily large. TD Ameritrade’s open architecture environment enables financial advisors like John Daly to select the technology they want to use. The lesson is that Daly could act as an entrepreneur and start his own firm while providing information technology with the scale that customers expect and providing the personal service that is often missing when dealing with larger organizations.[2][3][4]
This chapter focuses on the role of information technology (IT) in business, examining the details of MIS organization, as well as the challenges companies encounter in an increasingly technological world. As John Daly learned, harnessing the power of information technology gives a company a significant competitive advantage.
Transforming Businesses through Information
Information technology (IT) includes the equipment and techniques used to manage and process information. Information is at the heart of all organizations. Without information about the processes of and participants in an organization—including orders, products, inventory, scheduling, shipping, customers, suppliers, and employees—a business cannot operate.
In less than 70 years, we have shifted from an industrial society to a knowledge-based economy driven by information. Businesses depend on information technology for everything from running daily operations to making strategic decisions. Computers are the tools of this information age, performing extremely complex operations as well as everyday jobs such as word processing and creating spreadsheets. The pace of change has been rapid since the personal computer became a fixture on most office desks. Individual units became part of small networks, followed by more sophisticated enterprise-wide networks. figures 19.1 and 19.2 summarize the types of computer equipment and software, respectively, most commonly used in business management information systems today.
| Computer type | Description | Comments |
|---|---|---|
| Tablets | Self-contained computers in which applications (apps) can reside. These devices can also be linked into a network over which other programs can be accessed. | Increasing power, speed, and memory accessed via the cloud make these tablets the dominant computer for many business processes. |
| Desktop personal computers (PC) | Self-contained computers on which software can reside. These PCs can also be linked into a network over which other programs can be accessed. | Increasing power, speed, memory, and storage make these commonly used for many business processes. Can handle text, audio, video, and complex graphics. |
| Laptop computers | Portable computers similar in power to desktop computers. | Smaller size and weight make mobile computing easier for workers. |
| Minicomputers | Medium-sized computers with multiple processors, able to support from four to about 200 users at once. | The distinction between the larger minicomputers and smaller mainframes is blurring. |
| Miniframe computers | Large machines about the size of a refrigerator; can simultaneously run many different programs and support hundreds or thousands of users. | Extremely reliable and stable, these are used by companies and governments to process large amounts of data. They are more secure than PCs. |
| Servers | Greatest storage capacity and processing speeds. | These are subject to crashes and can be upgraded and repaired while operating. |
| Supercomputers | Most powerful computers, now capable of operating at speeds of 280 trillion calculations per second. | Companies can rent time to run projects from special supercomputer centers. |
Figure 19.1: Business computing equipment.
| Application type | Description |
|---|---|
| Word processing software | Used to write, edit, and format documents such as letters and reports. Spelling and grammar checkers, mail merge, tables, and other tools simplify document preparation. |
| Spreadsheet software | Used for preparation and analysis of financial statements, sales forecasts, budgets, and similar numerical and statistical data. Once the mathematical formulas are keyed into the spreadsheet, the data can be changed and the solution will be recalculated instantaneously. |
| Database management programs | Serve as electronic filing cabinets for records such as customer lists, employee data, and inventory information. Can sort data based on various criteria to create different reports. |
| Graphics and presentation programs | Create tables, graphs, and slides for customer presentations and reports. Can add images, video, animation, and sound effects. |
| Desktop publishing software | Combines word processing, graphics, and page layout software to create documents. Allows companies to design and produce sales brochures, catalogs, advertisements, and newsletters in-house. |
| Communications programs | Translate data into a form for transmission and transfer it across a network to other computers. Used to send and retrieve data and files. |
| Integrated software suites | Combine several popular types of programs, such as word processing, spreadsheet, database, graphics presentation, and communications programs. Component programs are designed to work together. |
| Groupware | Facilitates collaborative efforts of workgroups so that several people in different locations can work on one project. Supports online meetings and project management (scheduling, resource allocation, document and e-mail distribution, etc.). |
| Financial software | Used to compile accounting and financial data and create financial statements and reports. |
Figure 19.2: Business computing software.
Although most workers spend their days at powerful desktop computers, other groups tackle massive computational problems at specialized supercomputer centers. Tasks that would take years on a PC can be completed in just hours on a supercomputer. With their ability to perform complex calculations quickly, supercomputers play a critical role in national security research, such as analysis of defense intelligence; scientific research, from biomedical experiments and drug development to simulations of earthquakes and star formations; demographic studies such as analyzing and predicting voting patterns; and weather and environmental studies. Businesses, too, put supercomputers to work by analyzing big data to gain insights into customer behavior, improving inventory and production management and for product design.[5]
The speed of these special machines has been rising steadily to meet increasing demands for greater computational capabilities, and the next goal is quadrillions of computations per second, or petaflops. Achieving these incredible speeds is critical to future scientific, medical, and business discoveries. Many countries, among them the United States, China, France, and Japan, have made petascale computing a priority.[6]
In addition to a business’s own computers and internal networks, the internet makes it effortless to connect quickly to almost anyplace in the world. As Thomas Friedman points out in his book The World Is Flat, “We are now connecting all of the knowledge centers on the planet together into a single global network, which . . . could usher in an amazing era of prosperity and innovation.”[7]
The opportunities for collaboration on a global scale increase daily. A manager can share information with hundreds of thousands of people worldwide as easily as with a colleague on another floor of the same office building. The internet and the web have become indispensable business tools that facilitate communication within companies as well as with customers.
The rise of electronic trading hubs is just one example of how technology is facilitating the global economy. Electronic trading hubs are not reserved for large companies of developed economies, however. Alibaba is piloting an e-hub called eWTP in Malaysia that will provide access to small businesses. As Jack Ma, Alibaba co-founder, said at eWTP’s launch, “There are a lot of free-trade zones for efficient trade facilitation, but only for big companies. There is no free-trade zone designed for small companies. I have been shouting everywhere, screaming, that every government should do it.”[8]

Many companies entrust an executive called the chief information officer (CIO) with the responsibility of managing all information resources. The importance of this responsibility is immense. In addition to the massive expansion of information gathered by today’s businesses, most of us are knowledge workers who develop or use knowledge. Knowledge workers contribute to and benefit from information they use to perform planning, acquiring, searching, analyzing, organizing, storing, programming, producing, distributing, marketing, or selling functions. We must know how to gather and use information from the many resources available to us.
In today’s high-tech world, CIOs must possess not only the technical smarts to implement global IT infrastructures, integrate communications systems with partners, and protect customer data from insidious hackers, but they must also have strong business acumen. Google’s acclaimed tech chief Ben Fried manages the technology necessary to deliver more than 9 billion searches daily, with an eye towards greater business efficiency, growth, and profits.
Because most jobs today depend on information—obtaining, using, creating, managing, and sharing it—this chapter begins with the role of information in decision-making and goes on to discuss computer networks and management information systems. The management of information technology—planning and protection—follows. Finally, we’ll look at the latest trends in information technology. Throughout the chapter, examples show how managers and their companies are using computers to make better decisions in a highly competitive world.
Data and Information Systems
Information systems and the computers that support them are so much a part of our lives that we almost take them for granted. These management information systems methods and equipment that provide information about all aspects of a firm’s operations provide managers with the information they need to make decisions. They help managers properly categorize and identify ideas that result in substantial operational and cost benefits.
Businesses collect a great deal of data—raw, unorganized facts that can be moved and stored—in their daily operations. Only through well-designed IT systems and the power of computers can managers process these data into meaningful and useful information and use it for specific purposes, such as making business decisions. One such form of business information is the database, an electronic filing system that collects and organizes data and information. Using software called a database management system (DBMS), you can quickly and easily enter, store, organize, select, and retrieve data in a database. These data are then turned into information to run the business and to perform business analysis.
Databases are at the core of business information systems. For example, a customer database containing name, address, payment method, products ordered, price, order history, and similar data provides information to many departments. Marketing can track new orders and determine what products are selling best; sales can identify high-volume customers or contact customers about new or related products; operations managers use order information to obtain inventory and schedule production of the ordered products; and finance uses sales data to prepare financial statements. Later in the chapter, we will see how companies use very large databases called data warehouses and data marts.
Companies are discovering that they can’t operate well with a series of separate information systems geared to solving specific departmental problems. It takes a team effort to integrate the systems described and involves employees throughout the firm. Company-wide enterprise resource planning (ERP) systems that bring together human resources, operations, and technology are becoming an integral part of business strategy. So is managing the collective knowledge contained in an organization, using data warehouses and other technology tools. Technology experts are learning more about the way the business operates, and business managers are learning to use information systems technology effectively to create new opportunities and reach their goals.
In summary, businesses depend on information technology for everything from running daily operations to making strategic decisions. Companies must have management information systems that gather, analyze, and distribute information to the appropriate parties, including employees, suppliers, and customers. These systems are comprised of different types of computers that collect data and process it into usable information for decision-making. Managers tap into databases to access the information they need, whether for placing inventory orders, scheduling production, or preparing long-range forecasts. They can compare information about the company’s current status to its goals and standards. Company-wide enterprise resource planning systems that bring together human resources, operations, and technology are becoming an integral part of business strategy.
Linking Up: Computer Networks

Today most businesses use networks to deliver information to employees, suppliers, and customers. A computer network is a group of two or more computer systems linked together by communications channels to share data and information. Today’s networks often link thousands of users and can transmit audio and video as well as data.
Networks include clients and servers. The client is the application that runs on a personal computer or workstation. It relies on a server that manages network resources or performs special tasks such as storing files, managing one or more printers, or processing database queries. Any user on the network can access the server’s capabilities.
By making it easy and fast to share information, networks have created new ways to work and increase productivity. They provide more efficient use of resources, permitting communication and collaboration across distance and time. With file-sharing, all employees, regardless of location, have access to the same information. Shared databases also eliminate duplication of effort. Employees at different sites can “screen-share” computer files, working on data as if they were in the same room. Their computers are connected by phone or cable lines, they all see the same thing on their display, and anyone can make changes that are seen by the other participants. The employees can also use the networks for videoconferencing.
Networks make it possible for companies to run enterprise software, large programs with integrated modules that manage all of the corporation’s internal operations. Enterprise resource planning systems run on networks. Typical subsystems include finance, human resources, engineering, sales and order distribution, and order management and procurement. These modules work independently and then automatically exchange information, creating a company-wide system that includes current delivery dates, inventory status, quality control, and other critical information. Let’s now look at the basic types of networks companies use to transmit data—local area networks and wide area networks—and popular networking applications such as intranets and virtual private networks.
Connecting Near and Far with Networks
Two basic types of networks are distinguished by the area they cover. A local area network (LAN) lets people at one site exchange data and share the use of hardware and software from a variety of computer manufacturers. LANs offer companies a more cost-effective way to link computers than linking terminals to a mainframe computer. The most common uses of LANs at small businesses, for example, are office automation, accounting, and information management. LANs can help companies reduce staff, streamline operations, and cut processing costs. LANs can be set up with wired or wireless connections.
A wide area network (WAN) connects computers at different sites via telecommunications media such as phone lines, satellites, and microwaves. A modem connects the computer or a terminal to the telephone line and transmits data almost instantly, in less than a second. The internet is essentially a worldwide WAN. Communications companies, such as AT&T, Verizon, and Sprint, operate very large WANs. Companies also connect LANs at various locations into WANs. WANs make it possible for companies to work on critical projects around the clock by using teams in different time zones.
Several forms of WANs—intranets, virtual private networks (VPN), and extranets—use internet technology. Here we’ll look at intranets, internal corporate networks that are widely available in the corporate world, and VPNs. Although wireless networks have been around for more than a decade, they are increasing in use because of falling costs, faster and more reliable technology, and improved standards. They are similar to their wired LAN and WAN cousins, except they use radio frequency signals to transmit data. You use a wireless WAN (WWAN) regularly when you use your cellular phone. WANs’ coverage can span several countries. Telecommunications carriers operate using wireless WANs.
Wireless LANs (WLAN) that transmit data at one site offer an alternative to traditional wired systems. WLANs’ reach is a radius of 500 feet indoors and 1,000 feet outdoors and can be extended with antennas, transmitters, and other devices. The wireless devices communicate with a wired access point into the wired network. WLANs are convenient for specialized applications where wires are in the way or when employees are in different locations in a building. Hotels, airports, restaurants, hospitals, retail establishments, universities, and warehouses are among the largest users of WLANs, also known as Wi-Fi. For example, the Veterans Administration Hospital in West Haven, Connecticut, recently added Wi-Fi access in all patient rooms to upgrade its existing WLAN to improve patient access, quality, and reliability. The new WLAN supports many different functions, from better on-site communication among doctors and nurses through both data transmission and voice-over-internet phone systems to data-centric applications such as its Meditech clinical information system and pharmacy management.[12]
Catching the Entrepreneurial Spirit: Documenting the Future
Potential customers of Captiva Software didn’t share company cofounder and chief executive Reynolds Bish’s belief that paper wasn’t going away. They held to the idea that personal computers and the internet would make paper disappear, and they weren’t going to invest in software to organize their documents. That almost caused Captiva to go under. “We really were afraid we weren’t going to make it,” said Jim Berglund, an early investor in Captiva and a former board member.
But Bish asked investors for another $4 million commitment—on a bet that paper was here to stay. Bish recalls a board member telling him, “Five years from now people are going to either think you’re a genius or a complete idiot.”
That conversation took place 20 years ago. Captiva Software was named one of the fastest-growing technology companies in San Diego in the early 2000s for its 172 percent increase in revenues. The company was then acquired by EMC Corp.—the sixth-largest software company in the world and top maker of corporate data-storage equipment, with projected annual revenues of more than $9 billion—for $275 million in cash, rewarding embattled early Captiva investors with 10 times their money back. (In 2016, Dell acquired EMC for more than $67 billion.)
Captiva began its journey to the big time in 1989 in Park City, Utah, as TextWare Corp., a small data-entry company. Cofounder Steven Burton’s technical expertise, Bish’s business background, and a credit card helped them get the business going. “It was pure bootstrapping,” Bish said. “We did everything from going without a salary for a year or more to using up our credit cards.”
Bish and Burton quickly saw the need for employees to enter data more directly and accurately. The software they developed still required clerks to type information from a paper document, but it could check for inaccuracies, matching zip codes to cities, for instance. In 1996, TextWare produced software that could “read” typewritten words on a scanned piece of paper, which significantly reduced the number of data-entry clerks needed. It found popularity with credit-card processors, insurance companies, shipping companies, and other corporations that handled thousands of forms every day.
TextWare acquired or merged with five firms, went public, changed its name twice, and in 1998 set up its headquarters in San Diego, California, after buying Wheb Systems, which is based there. In 2002, the company merged with publicly held ActionPoint, a San Jose, California, document-processing company, and changed its name to Captiva.
An estimated 80 percent of all information is still paper-based, according to market research firm Forrester Research. Captiva’s flagship products, InputAccel and FormWare, process over 85 million pieces of paper worldwide every day, leaving no doubt that Bish’s vision was on target. Paper is indeed here to stay.[13][14][15][16][17][18]
An Inside Job: Intranets
Like LANs, intranets are private corporate networks. Many companies use both types of internal networks. However, because they use internet technology to connect computers, intranets are WANs that link employees in many locations and with different types of computers. Essentially mini-internets that serve only the company’s employees, intranets operate behind a firewall that prevents unauthorized access. Employees navigate using a standard web browser, which makes the intranet easy to use. They are also considerably less expensive to install and maintain than other network types and take advantage of the internet’s interactive features such as chat rooms and team workspaces. Many software providers now offer off-the-shelf intranet packages so that companies of all sizes can benefit from the increased access to and distribution of information.
Companies now recognize the power of intranets to connect employers and employees in many ways, promoting teamwork and knowledge-sharing. Intranets have many applications, from human resource (HR) administration to logistics. For instance, a benefits administration intranet can become a favorite with employees. Instead of having to contact an HR representative to make any changes in personnel records or retirement plan contributions or to submit time sheets, staff members simply log on to the intranet and update the information themselves. Managers can also process staffing updates, performance reviews, and incentive payments without filing paperwork with human resources. Employees can regularly check an online job board for new positions. Shifting routine administrative tasks to the intranet can bring additional benefits such as reducing the size of the HR department by 30 percent and allowing HR staff members to turn their attention to more substantive projects.[19]
Enterprise Portals Open the Door to Productivity
Intranets that take a broader view serve as sophisticated knowledge management tools.
One such intranet is the enterprise portal, an internal website that provides proprietary corporate information to a defined user group. Portals can take one of three forms: business to employee (B2E), business to business (B2B), and business to consumer (B2C). Unlike a standard intranet, enterprise portals allow individuals or user groups to customize the portal home page to gather just the information they need for their particular job situations and deliver it through a single web page. Because of their complexity, enterprise portals are typically the result of a collaborative project that brings together designs developed and perfected through the effort of HR, corporate communications, and information technology departments.
More companies use portal technology to provide:
- A consistent, simple user interface across the company
- Integration of disparate systems and multiple sets of data and information
- A single source for accurate and timely information that integrates internal and external information
- A shorter time to perform tasks and processes
- Cost savings through the elimination of information intermediaries
- Improved communications within the company and with customers, suppliers, dealers, and distributors
No More Tangles: Wireless Technologies
Wireless technology has become commonplace today. We routinely use devices such as cellular phones, mobile devices, garage door openers, and television remote controls—without thinking of them as examples of wireless technology. Businesses use wireless technologies to improve communications with customers, suppliers, and employees.
Companies in the package delivery industry, such as UPS and FedEx, were among the first users of wireless technology. Delivery personnel use handheld computers to send immediate confirmation of package receipt. You may also have seen meter readers and repair personnel from utility and energy companies send data from remote locations back to central computers.

Bluetooth short-range wireless technology is a global standard that improves personal connectivity for users of mobile phones, portable computers, and stereo headsets, and Bluetooth wirelessly connects keyboards and mice to computers and headsets to phones and music players. A Bluetooth-enabled mobile phone, for example, provides safer hands-free phone use while driving. The technology is finding many applications in the auto industry as well. Bluetooth wireless technology is now standard in many vehicles today. Many car, technology, and cell phone companies—among them Amazon, Apple, Audi, BMW, DaimlerChrysler, Google, Honda, Saab, Toyota, and Volkswagen—already offer Bluetooth hands-free solutions. Other uses include simplifying the connection of portable digital music players to the car’s audio system and transferring downloaded music to the system.[20]
Although designing a true mobile replacement for the desktop PC has proved elusive for computer manufacturers, ultramobile PCs offer wireless functions many professionals want—web browsing, e-mail, Microsoft Office, and telephony. The Apple iPad Pro runs iOS 10, and with its 10.5-inch LCD touch screen and stylus, the mini-tablet provides the power of a desktop PC and freedom from pen and paper.
Private Lines: Virtual Private Networks
Many companies use virtual private networks to connect two or more private networks (such as LANs) over a public network, such as the internet. VPNs include strong security measures to allow only authorized users to access the network and its sensitive corporate information. Companies with widespread offices may find that a VPN is a more cost-effective option than creating a network using purchased networking equipment and leasing expensive private lines. This type of private network is more limited than a VPN, because it doesn’t allow authorized users to connect to the corporate network when they are at home or traveling.

As figure 19.6 shows, the VPN uses existing internet infrastructure and equipment to connect remote users and offices almost anywhere in the world—without long-distance charges. In addition to saving on telecommunications costs, companies using VPNs don’t have to buy or maintain special networking equipment and can outsource management of remote access equipment. VPNs are useful for salespeople and telecommuters, who can access the company’s network as if they were on-site at the company’s office. On the downside, the VPN’s availability and performance, especially when it uses the internet, depends on factors largely outside of an organization’s control.
VPNs are popular with many different types of organizations. Why? Security is one of the main reasons to always use a VPN to access the internet. Because all your data is encrypted once tunneled, if a hacker were trying to intercept your browsing activity, say, while you were entering your credit card number to make an online purchase, the encryption would stymie their efforts. That’s why it’s a particularly good idea to use VPNs in public settings such as coffee shops and airports.[21]
With the increase need for privacy and security, there are a number of different VPN service providers that have emerged in recent years offering various subscription plans. NordVPN is one example. NordVPN was launched in 2012 by childhood friends and within 10 years became known as the “world’s leading VPN trusted by millions of people all over the globe”.[22]
Software on Demand: Application Service Providers
As software developers release new types of application programs and updated versions of existing ones every year or two, companies have to analyze whether they can justify buying or upgrading to the new software—in terms of both cost and implementation time. Application service providers (ASPs) offer a different approach to this problem. Companies subscribe, usually on a monthly basis, to an ASP and use the applications much like you’d use telephone voice mail, the technology for which resides at the phone company. Other names for ASPs include on-demand software, hosted applications, and software-as-a-service. Figure 19.7 shows how the ASP interfaces with software and hardware vendors and developers, the IT department, and users.
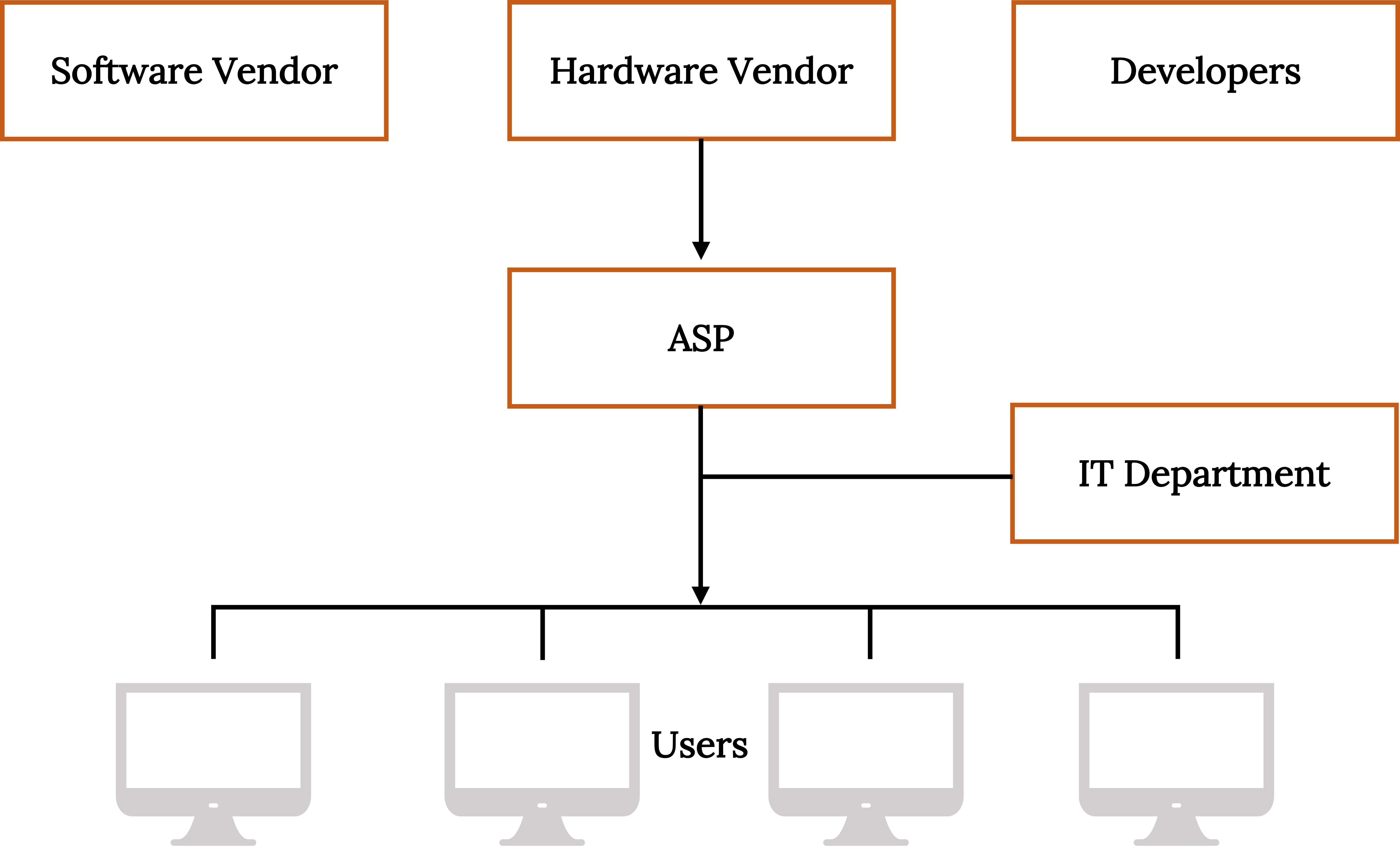
The simplest ASP applications are automated—for example, a user might use one to build a simple e-commerce site. ASPs provide three major categories of applications to users:
- Enterprise applications, including customer relationship management (CRM), enterprise resource planning, e-commerce, and data warehousing
- Collaborative applications for internal communications, e-mail, groupware, document creation, and management messaging
- Applications for personal use—for example, games, entertainment software, and home-office applications
According to recent surveys, more companies are currently using an ASP, and even moving their legacy systems to the cloud. Estimates suggest revenues from subscriptions to on-demand cloud services were about $180 billion in 2017. This sector is growing much more rapidly—three times faster—than traditional hardware and software.[23]
As this market grows, more companies are adding on-demand offerings to their traditional software packages. Amazon (Amazon Web Services), IBM, Microsoft, and Salesforce.com are among the leading cloud service providers.[24]
Until recently, many companies were reluctant to outsource critical enterprise applications to third-party providers. As ASPs improved their technologies and proved to be reliable and cost-effective, attitudes have changed. Companies, both large and small, seek cost advantages such as the convenience ASPs provide. The basic idea behind subscribing to an ASP is compelling. Users can access any of their applications and data from any computer, and IT can avoid purchasing, installing, supporting, and upgrading expensive software applications. ASPs buy and maintain the software on their servers and distribute it through high-speed networks. Subscribers rent the applications they want for a set period of time and price. The savings in licensing fees, infrastructure, time, and staff are significant.
Managed service providers (MSPs) represent the next generation of ASPs, offering greater customization and expanded capabilities that include business processes and complete management of the network servers. The global market for managed IT services reached $149.1 billion in 2016. This market is estimated to reach $256.5 billion in 2021, from $166.7 billion in 2017, at a compound annual growth rate of 11.5 percent for the period 2018 through 2021.[25]
In summary, today companies use networks of linked computers that share data and expensive hardware to improve operating efficiency. Types of networks include local area networks, wide area networks, and wireless local area networks. Intranets are private WANs that allow a company’s employees to communicate quickly with one other and work on joint projects, regardless of their location. Companies are finding new uses for wireless technologies such as tablets, cell phones, and other mobile devices. Virtual private networks give companies a cost-effective secure connection between remote locations by using public networks such as the internet.
Management Information Systems
Whereas individuals use business productivity software such as word processing, spreadsheet, and graphics programs to accomplish a variety of tasks, the job of managing a company’s information needs falls to management information systems: users, hardware, and software that support decision-making. Information systems collect and store the company’s key data and produce the information managers need for analysis, control, and decision-making.
Factories use computer-based information systems to automate production processes and order and monitor inventory. Most companies use them to process customer orders and handle billing and vendor payments. Banks use a variety of information systems to process transactions such as deposits, ATM withdrawals, and loan payments. Most consumer transactions also involve information systems. When you check out at the supermarket, book a hotel room online, or download music over the internet, information systems record and track the transaction and transmit the data to the necessary places.
Companies typically have several types of information systems, starting with systems to process transactions. Management support systems are dynamic systems that allow users to analyze data to make forecasts, identify business trends, and model business strategies. Office automation systems improve the flow of communication throughout the organization. Each type of information system serves a particular level of decision-making: operational, tactical, and strategic. Figure 19.8 shows the relationship between transaction processing and management support systems as well as the management levels they serve. Let’s take a more detailed look at how companies and managers use transaction processing and management support systems to manage information.
Transaction Processing Systems
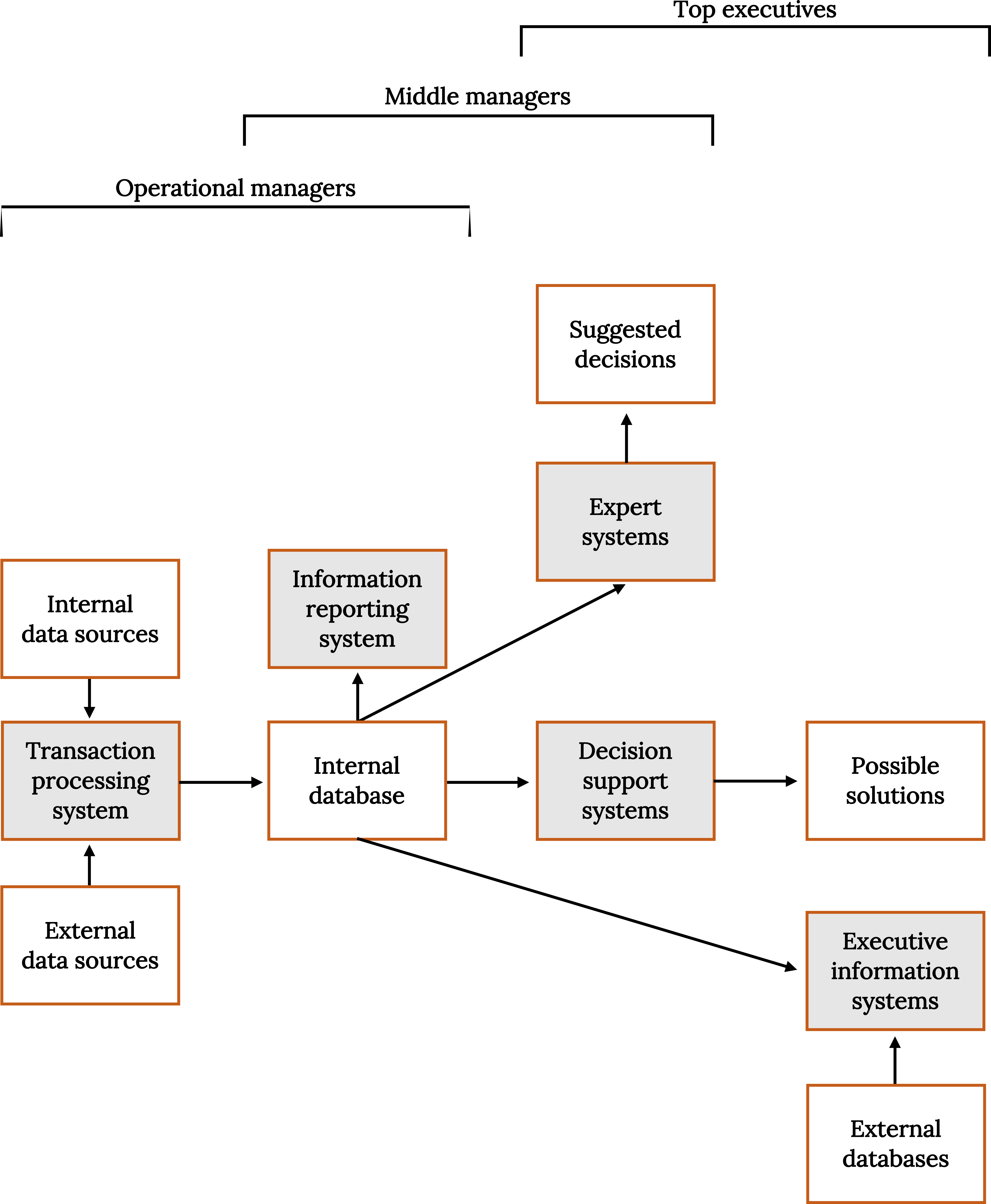
A firm’s integrated information system starts with its transaction processing system (TPS). The TPS receives raw data from internal and external sources and prepares these data for storage in a database similar to a microcomputer database but vastly larger. In fact, all the company’s key data are stored in a single huge database that becomes the company’s central information resource. As noted earlier, the database management system tracks the data and allows users to query the database for the information they need.
The database can be updated in two ways: batch processing, where data are collected over some time period and processed together, and online, or real-time, processing, which processes data as they become available. Batch processing uses computer resources very efficiently and is well-suited to applications such as payroll processing that require periodic rather than continuous processing. Online processing keeps the company’s data current. When you make an airline reservation, the information is entered into the airline’s information system, and you quickly receive confirmation, typically through an e-mail. Online processing is more expensive than batch processing, so companies must weigh the cost versus the benefit. For example, a factory that operates around the clock may use real-time processing for inventory and other time-sensitive requirements but process accounting data in batches overnight.
Decisions, Decisions: Management Support Systems
Transaction processing systems automate routine and tedious back-office processes such as accounting, order processing, and financial reporting. They reduce clerical expenses and provide basic operational information quickly. Management support systems (MSSs) use the internal master database to perform high-level analyses that help managers make better decisions.
Information technologies such as data warehousing are part of more advanced MSSs. A data warehouse combines many databases across the whole company into one central database that supports management decision-making. With a data warehouse, managers can easily access and share data across the enterprise to get a broad overview rather than just isolated segments of information. Data warehouses include software to extract data from operational databases, maintain the data in the warehouse, and provide data to users. They can analyze data much faster than transaction-processing systems. Data warehouses may contain many data marts, special subsets of a data warehouse that each deal with a single area of data. Data marts are organized for quick analysis.
Companies use data warehouses to gather, secure, and analyze data for many purposes, including customer relationship management systems, fraud detection, product-line analysis, and corporate asset management. Retailers might wish to identify customer demographic characteristics and shopping patterns to improve direct-mailing responses. Banks can more easily spot credit-card fraud, as well as analyze customer usage patterns.
According to Forrester Research, about 60 percent of companies with $1 billion or more in revenues use data warehouses as a management tool. Union Pacific (UP), a $19 billion railroad, turned to data warehouse technology to streamline its business operations. By consolidating multiple separate systems, UP achieved a unified supply-chain system that also enhanced its customer service. “Before our data warehouse came into being we had stovepipe systems,” says Roger Bresnahan, principal engineer. “None of them talked to each other. . . . We couldn’t get a whole picture of the railroad.”
UP’s data warehouse system took many years and the involvement of 26 departments to create. The results were well worth the effort: UP can now make more accurate forecasts, identify the best traffic routes, and determine the most profitable market segments. The ability to predict seasonal patterns and manage fuel costs more closely has saved UP millions of dollars by optimizing locomotive and other asset utilization and through more efficient crew management. In just three years, Bresnahan reports, the data warehouse system had paid for itself.[26]
At the first level of an MSS is an information-reporting system, which uses summary data collected by the TPS to produce both regularly scheduled and special reports. The level of detail would depend on the user. A company’s payroll personnel might get a weekly payroll report showing how each employee’s paycheck was determined. Higher-level mangers might receive a payroll summary report that shows total labor cost and overtime by department and a comparison of current labor costs with those in the prior year. Exception reports show cases that fail to meet some standard. An accounts receivable exception report that lists all customers with overdue accounts would help collection personnel focus their work. Special reports are generated only when a manager requests them; for example, a report showing sales by region and type of customer can highlight reasons for a sales decline.
Decision Support Systems

A decision support system (DSS) helps managers make decisions using interactive computer models that describe real-world processes. The DSS also uses data from the internal database but looks for specific data that relate to the problems at hand. It is a tool for answering “what if” questions about what would happen if the manager made certain changes. In simple cases, a manager can create a spreadsheet and try changing some of the numbers. For instance, a manager could create a spreadsheet to show the amount of overtime required if the number of workers increases or decreases. With models, the manager enters into the computer the values that describe a particular situation, and the program computes the results. Marketing executives at a furniture company could run DSS models that use sales data and demographic assumptions to develop forecasts of the types of furniture that would appeal to the fastest-growing population groups.
Companies can use a predictive analytics program to improve their inventory management system and use big data to target customer segments for new products and line extensions.
Decision support systems help businesses by providing quantitative data and predictive models that aid problem-solving and decision-making. Now the health-care industry wants this technology in hospitals to improve the practice of medicine. Spearheading the effort for a clinical decision-support system is the American Medical Informatics Association, which believes a national DSS could help physicians with diagnosing and treating illnesses.
Executive Information Systems
Although similar to a DSS, an executive information system (EIS) is customized for an individual executive. These systems provide specific information for strategic decisions. For example, a CEO’s EIS may include special spreadsheets that present financial data comparing the company to its principal competitors and graphs showing current economic and industry trends.
Expert Systems
An expert system gives managers advice similar to what they would get from a human consultant. Artificial intelligence enables computers to reason and learn to solve problems in much the same way humans do, using what-if reasoning. Although they are expensive and difficult to create, expert systems are finding their way into more companies as more applications are found. Lower-end expert systems can even run on mobile devices. Top-of-the-line systems help airlines appropriately deploy aircraft and crews, critical to the carriers’ efficient operations. The cost of hiring enough people to do these ongoing analytical tasks would be prohibitively expensive. Expert systems have also been used to help explore for oil, schedule employee work shifts, and diagnose illnesses. Some expert systems take the place of human experts, whereas others assist them.
In summary, a management information system consists of a transaction processing system, management support systems, and an office automation system. The transaction processing system collects and organizes operational data on the firm’s activities. Management support systems help managers make better decisions. They include an information-reporting system that provides information based on the data collected by the TPS to the managers who need it; decision support systems that use models to assist in answering “what if” types of questions; and expert systems that give managers advice similar to what they would get from a human consultant. Executive information systems are customized to the needs of top management.
Technology Management and Planning
With the help of computers, people have produced more data in the last 30 years than in the previous 5,000 years combined. Companies today make sizable investments in information technology to help them manage this overwhelming amount of data, convert the data into knowledge, and deliver it to the people who need it. In many cases, however, the companies do not reap the desired benefits from these expenditures. Among the typical complaints from senior executives are that the company is spending too much and not getting adequate performance and payoff from IT investments, these investments do not relate to business strategy, the firm seems to be buying the latest technology for technology’s sake, and communications between IT specialists and IT users are poor.
Optimize IT!
Managing a company’s enterprise-wide IT operations, especially when those often stretch across multiple locations, software applications, and systems, is no easy task. IT managers must deal not only with on-site systems; they must also oversee the networks and other technology, such as mobile devices that handle e-mail messaging, that connect staff working at locations ranging from the next town to another continent. At the same time, IT managers face time constraints and budget restrictions, making their jobs even more challenging.
Growing companies may find themselves with a decentralized IT structure that includes many separate systems and duplication of efforts. A company that wants to enter or expand into e-commerce needs systems flexible enough to adapt to this changing marketplace. Security for equipment and data is another critical area, which we will cover later in the chapter.
The goal is to develop an integrated, company-wide technology plan that balances business judgment, technology expertise, and technology investment. IT planning requires a coordinated effort among a firm’s top executives, IT managers, and business-unit managers to develop a comprehensive plan. Such plans must take into account the company’s strategic objectives and how the right technology will help managers reach those goals.
Technology management and planning go beyond buying new technology. Today companies are cutting IT budgets so that managers are being asked to do more with less. They are implementing projects that leverage their investment in the technology they already have, finding ways to maximize efficiency and optimize utilization.
Managing Knowledge Resources
As a result of the proliferation of information, we are also seeing a major shift from information management to a broader view that focuses on finding opportunities in and unlocking the value of intellectual rather than physical assets. Whereas information management involves collecting, processing, and condensing information, the more difficult task of knowledge management (KM) focuses on researching, gathering, organizing, and sharing an organization’s collective knowledge to improve productivity, foster innovation, and gain competitive advantage. Some companies are even creating a new position, chief knowledge officer, to head up this effort.[27]
Companies use their IT systems to facilitate the physical sharing of knowledge. But better hardware and software are not the answer to KM. KM is not technology-based, but rather a business practice that uses technology. Technology alone does not constitute KM, nor is it the solution to KM. Rather, it facilitates KM. Executives with successful KM initiatives understand that KM is not a matter of buying a major software application that serves as a data depository and coordinates all of a company’s intellectual capital. According to Melinda Bickerstaff, vice president of knowledge management at Bristol-Myers Squibb (BMS), any such “leading with technology” approach is a sure path to failure. “Knowledge management has to be perceived as a business problem solver, not as an abstract concept,” Bickerstaff explains.
Effective KM calls for an interdisciplinary approach that coordinates all aspects of an organization’s knowledge. It requires a major change in behavior as well as technology to leverage the power of information systems, especially the internet, and a company’s human capital resources. The first step is creating an information culture through organizational structure and rewards that promotes a more flexible, collaborative way of working and communicating. Moving an organization toward KM is no easy task, but it is well worth the effort in terms of creating a more collaborative environment, reducing duplication of effort, and increasing shared knowledge. The benefits can be significant in terms of growth, time, and money.
At Bristol-Meyers Squibb, a major pharmaceutical company, Bickerstaff began the KM implementation by looking for specific information-related problems to solve so that the company would save time and/or money. For example, she learned that company scientists were spending about 18 percent of their time searching multiple databases to find patents and other information. Simply integrating the relevant databases gave researchers the ability to perform faster searches. A more complex project involved compiling the best practices of drug-development teams with the best FDA approval rates so that other groups could benefit. Rather than send forms that could be easily set aside, Bickenstaff arranged to conduct interviews and lessons-learned sessions. The information was then developed into interesting articles rather than dry corporate reports.[28]
Technology Planning
A good technology plan provides employees with the tools they need to perform their jobs at the highest levels of efficiency. The first step is a general needs assessment, followed by ranking of projects and the specific choices of hardware and software. Figure 19.10 poses some basic questions departmental managers and IT specialists should ask when planning technology purchases.
| Questions for IT project planning |
|---|
| What are the company’s overall objectives? |
| What problems does the company want to solve? |
| How can technology help meet those goals and solve the problems? |
| What are the company’s IT priorities, both short- and long-term? |
| What type of technology infrastructure (centralized or decentralized) best serves the company’s needs? |
| Which technologies meet the company’s requirements? |
| Are additional hardware and software required? If so, will they integrate with the company’s existing systems? |
| Does the system design and implementation include the people and process changes, in addition to the technological ones? |
| Do you have the in-house capabilities to develop and implement the proposed applications, or should you bring in an outside specialist? |
Figure 19.10: Questions for IT project planning.
Once managers identify the projects that make business sense, they can choose the best products for the company’s needs. The final step is to evaluate the potential benefits of the technology in terms of efficiency and effectiveness. For a successful project, you must evaluate and restructure business processes, choose technology, develop and implement the system, and manage the change processes to best serve your organizational needs. Installing a new IT system on top of inefficient business processes is a waste of time and money!
In summary, to get the most value from IT, companies must go beyond simply collecting and summarizing information. Technology planning involves evaluating the company’s goals and objectives and using the right technology to reach them. IT managers must also evaluate the existing infrastructure to get the best return on the company’s investment in IT assets. Knowledge management focuses on sharing an organization’s collective knowledge to improve productivity and foster innovation. Some companies establish the position of chief knowledge officer to head up KM activities.
Protecting Computers and Information
Have you ever lost a term paper you worked on for weeks because your hard drive crashed or you deleted the wrong file? You were upset, angry, and frustrated. Multiply that paper and your feelings hundreds of times over, and you can understand why companies must protect computers, networks, and the information they store and transmit from a variety of potential threats. For example, security breaches of corporate information systems—from human hackers or electronic versions such as viruses and worms—are increasing at an alarming rate. The ever-increasing dependence on computers requires plans that cover human error, power outages, equipment failure, hacking, and terrorist attacks. To withstand natural disasters such as major fires, earthquakes, and floods, many companies install specialized fault-tolerant computer systems.
Disasters are not the only threat to data. A great deal of data, much of it confidential, can easily be tapped or destroyed by anyone who knows about computers. Keeping your networks secure from unauthorized access—from internal as well as external sources—requires formal security policies and enforcement procedures. The increasing popularity of mobile devices—laptops, tablets, and cell phones—and wireless networks requires new types of security provisions.
In response to mounting security concerns, companies have increased spending on technology to protect their IT infrastructure and data. Along with specialized hardware and software, companies need to develop specific security strategies that take a proactive approach to prevent security and technical problems before they start. However, a recent CIO article lamented the lack of basic security policies that companies only implement after a hack or data crisis.[29]
Data Security Issues
Unauthorized access into a company’s computer systems can be expensive, and not just in monetary terms. Juniper Networks estimates that cybercrime will cost businesses more than $2 trillion in 2019, compared to just $450 million in 2001. The most costly categories of threats include worms, viruses, and Trojan horses (defined later in this section); computer theft; financial fraud; and unauthorized network access. The report also states that almost all U.S. businesses report at least one security issue, and almost 20 percent have experienced multiple security incidents.[30]
Computer crooks are becoming more sophisticated all the time, finding new ways to get into ultra-secure sites. “As companies and consumers continue to move towards a networked and information economy, more opportunity exists for cybercriminals to take advantage of vulnerabilities on networks and computers,” says Chris Christiansen, program vice president at technology research firm IDC.[31]

Whereas early cybercrooks were typically amateur hackers working alone, the new ones are more professional and often work in gangs to commit large-scale internet crimes for large financial rewards. The internet, where criminals can hide behind anonymous screen names, has increased the stakes and expanded the realm of opportunities to commit identity theft and similar crimes. Catching such cybercriminals is difficult, and fewer than 5 percent are caught.[32]
Data security is under constant attack. In 2017, cybercriminals penetrated Equifax, one of the largest credit bureaus in the nation, and stole the personal data of more than 145 million people. To date, it is considered one of the worst data breaches of all time because of the amount of sensitive data stolen, including consumers’ Social Security numbers.
Firms are taking steps to prevent these costly computer crimes and problems, which fall into several major categories:
- Unauthorized access and security breaches. Whether from internal or external sources, unauthorized access and security breaches are a top concern of IT managers. These can create havoc with a company’s systems and damage customer relationships. Unauthorized access also includes employees, who can copy confidential new-product information and provide it to competitors or use company systems for personal business that may interfere with systems operation. Networking links also make it easier for someone outside the organization to gain access to a company’s computers.
One of the latest forms of cybercrime involves secretly installing keylogging software via software downloads, e-mail attachments, or shared files. This software then copies and transmits a user’s keystrokes—passwords, PINs, and other personal information—from selected sites, such as banking and credit card sites, to thieves.
-
Computer viruses, worms, and Trojan horses. Computer viruses and related security problems such as worms and Trojan horses are among the top threats to business and personal computer security. A computer program that copies itself into other software and can spread to other computer systems, a computer virus can destroy the contents of a computer’s hard drive or damage files. Another form is called a worm because it spreads itself automatically from computer to computer. Unlike a virus, a worm doesn’t require e-mail to replicate and transmit itself into other systems. It can enter through valid access points.
Trojan horses are programs that appear to be harmless and from legitimate sources but trick the user into installing them. When run, they damage the user’s computer. For example, a Trojan horse may claim to get rid of viruses but instead infects the computer. Other forms of Trojan horses provide a “trapdoor” that allows undocumented access to a computer, unbeknownst to the user. Trojan horses do not, however, infect other files or self-replicate.[33]
Viruses can hide for weeks, months, or even years before starting to damage information. A virus that “infects” one computer or network can be spread to another computer by sharing disks or by downloading infected files over the internet. To protect data from virus damage, virus protection software automatically monitors computers to detect and remove viruses. Program developers make regular updates available to guard against newly created viruses. In addition, experts are becoming more proficient at tracking down virus authors, who are subject to criminal charges.
-
Deliberate damage to equipment or information. For example, an unhappy employee in the purchasing department could get into the company’s computer system and delete information on past orders and future inventory needs. The sabotage could severely disrupt production and the accounts payable system. Willful acts to destroy or change the data in computers are hard to prevent. To lessen the damage, companies should back up critical information.
-
Spam. Although you might think that spam, or unsolicited and unwanted e-mail, is just a nuisance, it also poses a security threat to companies. Viruses spread through e-mail attachments that can accompany spam e-mails. Spam is now clogging blogs, instant messages, and cell phone text messages as well as e-mail inboxes. Spam presents other threats to a corporation: lost productivity and expenses from dealing with spam, such as opening the messages and searching for legitimate messages that special spam filters keep out.
-
Software and media piracy. The copying of copyrighted software programs, games, and movies by people who haven’t paid for them is another form of unauthorized use. Piracy, defined as using software without a license, takes revenue away from the company that developed the program—usually at great cost. It includes making counterfeit CDs to sell as well as personal copying of software to share with friends.
Preventing Problems
Creating formal written information security policies to set standards and provide the basis for enforcement is the first step in a company’s security strategy. Unfortunately, a recent survey of IT executives worldwide revealed that over two-thirds expect a cyberattack in the near future. Stephanie Ewing, a data security expert, states, “Having a documented, tested process brings order to chaotic situations and keeps everyone focused on solving the most pressing issues.” Without information security strategies in place, companies spend too much time in a reactive mode—responding to crises—and don’t focus enough on prevention.[34]
Security plans should have the support of top management, and then follow with procedures to implement the security policies. Because IT is a dynamic field with ongoing changes to equipment and processes, it’s important to review security policies often. Some security policies can be handled automatically, by technical measures, whereas others involve administrative policies that rely on humans to perform them. Examples of administrative policies are “Users must change their passwords every 90 days” and “End users will update their virus signatures at least once a week.” [35]
| Percentage | Concern for protecting data |
|---|---|
| 52 | Aren’t sure how to secure connected devices and apps |
| 40 | Don’t immediately change default passwords |
| 33 | Don’t think they can control how companies collect personal information |
| 33 | Parents admit they don’t know the risks well enough to explain to children |
| 37 | Use credit-monitoring services |
Figure 19.11: Five areas of concern regarding the protection of data.
Preventing costly problems can be as simple as regularly backing up applications and data. Companies should have systems in place that automatically back up the company’s data every day and store copies of the backups off-site. In addition, employees should back up their own work regularly. Another good policy is to maintain a complete and current database of all IT hardware, software, and user details to make it easier to manage software licenses and updates and diagnose problems. In many cases, IT staff can use remote access technology to automatically monitor and fix problems, as well as update applications and services.
Companies should never overlook the human factor in the security equation. One of the most common ways that outsiders get into company systems is by posing as an employee, first getting the staffer’s full name and username from an e-mail message and then calling the help desk to ask for a forgotten password. Crooks can also get passwords by viewing them on notes attached to a desk or computer monitor, using machines that employees leave logged on when they leave their desks, and leaving laptop computers with sensitive information unsecured in public places.
Portable devices, from handheld computers to tiny plug-and-play flash drives and other storage devices (including mobile phones), pose security risks as well. They are often used to store sensitive data such as passwords, bank details, and calendars. Mobile devices can spread viruses when users download virus-infected documents to their company computers.
Imagine the problems that could arise if an employee saw a calendar entry on a mobile device like “meeting re: layoffs,” an outsider saw “meeting about merger with ABC Company,” or an employee lost a flash drive containing files about marketing plans for a new product. Manufacturers are responding to IT managers’ concerns about security by adding password protection and encryption to flash drives. Companies can also use flash drive monitoring software that prevents unauthorized access on PCs and laptops.
Companies have many ways to avoid an IT meltdown, as shown below:
- Develop a comprehensive plan and policies that include portable as well as fixed equipment.
- Protect the equipment itself with stringent physical security measures to the premises.
- Protect data using special encryption technology to encode confidential information so only the recipient can decipher it.
- Stop unwanted access from inside or outside with special authorization systems. These can be as simple as a password or as sophisticated as fingerprint or voice identification.
- Install firewalls, hardware or software designed to prevent unauthorized access to or from a private network.
- Monitor network activity with intrusion-detection systems that signal possible unauthorized access, and document suspicious events.
- Conduct periodic IT audits to catalog all attached storage devices as well as computers.
- Use technology that monitors ports for unauthorized attached devices and turn off those that are not approved for business use.
- Train employees to troubleshoot problems in advance, rather than just react to them.
- Hold frequent staff-training sessions to teach correct security procedures, such as logging out of networks when they go to lunch and changing passwords often.
- Make sure employees choose sensible passwords, at least six and ideally eight characters long, containing numbers, letters, and punctuation marks. Avoid dictionary words and personal information.
- Establish a database of useful information and FAQ (frequently asked questions) for employees so they can solve problems themselves.
- Develop a healthy communications atmosphere.
Keep IT Confidential: Privacy Concerns
The very existence of huge electronic file cabinets full of personal information presents a threat to our personal privacy. Until recently, our financial, medical, tax, and other records were stored in separate computer systems. Computer networks make it easy to pool these data into data warehouses. Companies also sell the information they collect about you from sources like warranty registration cards, credit-card records, registration at websites, personal data forms required to purchase online, and grocery store discount club cards. Telemarketers can combine data from different sources to create fairly detailed profiles of consumers.
The September 11, 2001, tragedy and other massive security breaches have raised additional privacy concerns. As a result, the government began looking for ways to improve domestic-intelligence collection and analyze terrorist threats within the United States. Sophisticated database applications that look for hidden patterns in a group of data, a process called data mining, increase the potential for tracking and predicting people’s daily activities. Legislators and privacy activists worry that such programs as this and ones that eavesdrop electronically could lead to excessive government surveillance that encroaches on personal privacy. The stakes are much higher as well: errors in data mining by companies in business may result in a consumer being targeted with inappropriate advertising, whereas a governmental mistake in tracking suspected terrorists could do untold damage to an unjustly targeted person.
Increasingly, consumers are fighting to regain control of personal data and how that information is used. Privacy advocates are working to block sales of information collected by governments and corporations. For example, they want to prevent state governments from selling driver’s license information and supermarkets from collecting and selling information gathered when shoppers use barcoded plastic discount cards. With information about their buying habits, advertisers can target consumers for specific marketing programs.
The challenge to companies is to find a balance between collecting the information they need while at the same time protecting individual consumer rights. Most registration and warranty forms that ask questions about income and interests have a box for consumers to check to prevent the company from selling their names. Many companies now state in their privacy policies that they will not abuse the information they collect. Regulators are taking action against companies that fail to respect consumer privacy.
In summary, because companies are more dependent on computers than ever before, they need to protect data and equipment from natural disasters and computer crime. Types of computer crime include unauthorized use and access, software piracy, malicious damage, and computer viruses. To protect IT assets, companies should prepare written security policies. They can use technology such as virus protection, firewalls, and employee training in proper security procedures. They must also take steps to protect customers’ personal privacy rights.
Trends in Information Technology
Information technology is a continually evolving field. The fast pace and amount of change, coupled with IT’s broad reach, make it especially challenging to isolate industry trends. From the time we write this chapter to the time you read it—as little as six months—new trends will appear, and those that seemed important may fade. However, some trends that are reshaping today’s IT landscape are digital forensics, the shift to a distributed workforce, and the increasing use of grid computing.
Cyber Sleuthing: A New Style of Crime Busting
What helped investigators bring suit against Enron, Merck’s Vioxx medication, and the BTK serial killer? Digital evidence taken from an individual’s computer or corporate network—web pages, pictures, documents, and e-mails are part of a relatively new science called digital forensics. Digital-forensics software safeguards electronic evidence used in investigations by creating a duplicate of a hard drive that an investigator can search by keyword, file type, or access date. Digital forensics is also evolving into areas such as cloud computing and blockchain technology. For instance, it is estimated that as much as 3.9 million of the original 21 million bitcoins are “lost” on hard drives confined to landfills and flash drives located in the back of old office desks.[36]
But nowadays digital sleuthing is not limited to law enforcement. Companies such as Walmart, Target, and American Express have their own secret in-house digital forensics teams. And what if you’re in New York and need to seize a hard drive in Hong Kong? No problem. Over 75 members of the Fortune 500 now use technology that allows them to search hard drives remotely over their corporate networks. Digital forensics makes it possible to track down those who steal corporate data and intellectual property. Broadcom, a semiconductor chip designer, used computer forensics to investigate and apprehend former employees who were attempting to steal trade secrets. In the process, Broadcom gathered incriminating e-mails, including deleted documents, that gave it solid evidence to use the 2013 Federal Computer Fraud and Abuse Act to stop the former employees from starting up a rival firm.[37][38]
However, there is a downside to having these advanced capabilities. If this kind of software falls into the wrong hands, sophisticated hackers could access corporate networks and individual computers as easily as taking candy from a baby—and the victims would not even know it was happening. In an age of corporate wrongdoing, sexual predators, and computer porn, your hard drive will tell investigators everything they need to know about your behavior and interests, good and bad. Cybersleuthing means we are all potential targets of digital forensics. As evidenced by the huge increase in identity theft, personal privacy—once an unassailable right—is no longer as sacred as it once was.
The Distributed Workforce
Insurance company Aetna shuttered 2.7 million square feet of office space, saving the company $78 million, while American Express estimates it saved between $10 to $15 million dollars per year by expanding its distributed workforce. Was this a sign that these company were in trouble? Far from it. Instead of maintaining expensive offices in multiple locations, they sent employees home to work and adopted a new model for employees: the distributed workforce. Employees have no permanent office space and work from home or on the road. The shift to virtual workers has been a huge success, and not only do companies save on their personnel and related costs, but they also have happier, more productive employees.
Aetna and American Express are not alone in recognizing the benefits of distributed workers, especially in companies that depend on knowledge workers. Work Design Collaborative LLC in Prescott, Arizona, estimates that about 12 percent of all workers in the United States fall into this category, and in urban areas the number could be as high as 15 percent. There are estimates that this trend could eventually reach 40 percent over the next decade, as long commutes, high gas costs, and better connecting tools and technologies make this an attractive option for many workers who like the flexibility of not working in an office.[39]
Already, employees use the internet to conduct video-conferenced meetings and collaborate on teams that span the globe. On the downside, working from home can also mean being available 24/7—although most workers consider the trade-off well worth it.
According to recent statistics, close to four million U.S. workers work from home at least half of the time. Remote workers continue to be recruited by companies of all sizes, including Amazon, Dell, Salesforce, and others.[40]
Intel has a successful virtual-work program that has been popular with working parents. “Technology allows working remotely to be completely invisible,” says Laura Dionne, the company’s director of supply-chain transformation. At Boeing, thousands of employees participate in the virtual-work program, and it has been a critical factor in attracting and retaining younger workers. Almost half of Sun Microsystems’ employees are “location-independent,” reducing real estate costs by $300 million. Additional benefits for Sun are higher productivity from these workers and the ability to hire the best talent. “Our people working these remote schedules are the happiest employees we have, and they have the lowest attrition rates,” says Bill MacGowan, senior vice president for human resources at Sun. “Would I rather settle on someone mediocre in the Bay Area, or get the best person in the country who is willing to work remotely?”[41]
Grid and Cloud Computing Offer Powerful Solutions
How can smaller companies that occasionally need to perform difficult and large-scale computational tasks find a way to accomplish their projects? They can turn to grid or cloud computing, also called utility computing or peer-to-peer computing. Cloud and grid technology provides a way to divide the job into many smaller tasks and distribute them to a virtual supercomputer consisting of many small computers linked into a common network. Combining multiple desktop machines results in computing power that exceeds supercomputer speeds. A hardware and software infrastructure clusters and integrates computers and applications from multiple sources, harnessing unused power in existing PCs and networks. This structure distributes computational resources but maintains central control of the process. A central server acts as a team leader and traffic monitor. The controlling cluster server divides a task into subtasks, assigns the work to computers on the grid with surplus processing power, combines the results, and moves on to the next task until the job is finished. Figure 19.12 shows how typical grid and cloud setups work, and the differences between the two.
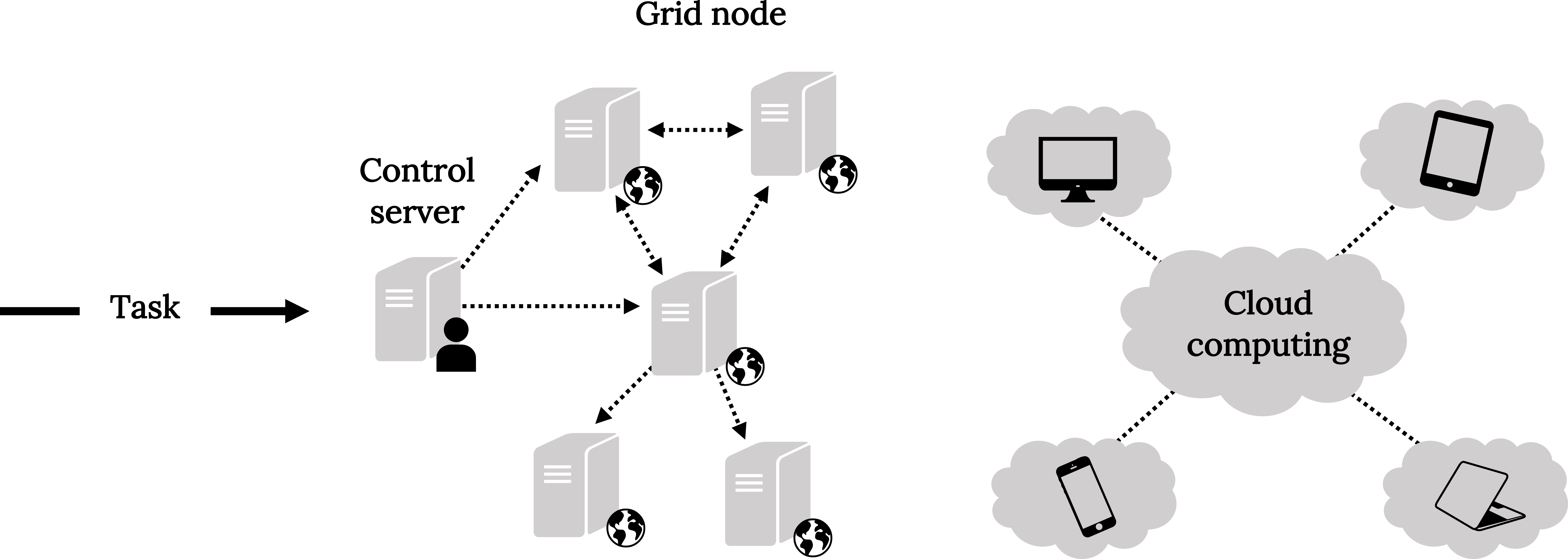
With utility computing, any company—large or small—can access the software and computer capacity on an as-needed basis. One of the big advantages of cloud computing is that companies can update their inventory in real time across their entire organization. For example, suppose you are an appliance retailer and have several outlets throughout the Midwest. If you have one model of a Whirlpool washing machine in your Des Moines, Iowa, store, and a salesperson in your Chicago location can sell that model in Chicago, the sale can be accomplished pretty easily. They can finalize the sale, create the shipping instructions, and update the inventory record automatically—and the Chicago consumer’s needs will be met.[42]
Amazon, Google, IBM, Salesforce.com, Oracle, and Hewlett-Packard Enterprise are among the companies providing as-needed cloud and grid services. Although cloud and grid computing appears similar to outsourcing or on-demand software from ASPs, it has two key differences:
- Pricing is set per-use, whereas outsourcing involves fixed-price contracts.
- Cloud and grid computing goes beyond hosted software and includes computer and networking equipment as well as services.
The cloud and grids provide a very cost-effective way to provide computing power for complex projects in areas such as weather research and financial and biomedical modeling. Because the computing infrastructure already exists—they tap into computer capacity that is otherwise unused—the cost is quite low. The increased interest in cloud and grid technology will continue to contribute to high growth.
In summary, IT is a dynamic industry, and companies must stay current on the latest trends to identify ones that help them maintain their competitive edge, such as digital forensics, the distributed workforce, and grid computing. With digital forensics techniques, corporations, government agencies, attorneys, and lawmakers can obtain evidence from computers and corporate networks—web pages, pictures, documents, and e-mails. Many knowledge workers now work remotely rather than from an office. Companies adopting the distributed workforce model gain many benefits, such as cost savings, more satisfied and productive employees, and increased employee retention. Cloud computing harnesses the power of computers, online software, and data storage to create a virtual computing environment that is invisible to the user. A company can access the cloud on an as-needed basis instead of investing in its own supercomputer equipment. Outsourcing a portion of the company’s computing needs provides additional flexibility and cost advantages. Companies can also set up internal grids.
Key Takeaways
- Using software called a database management system (DBMS), you can quickly and easily enter, store, organize, select, and retrieve data in a database. These data are then turned into information to run the business and to perform business analysis.
- Databases are an electronic filing system that collects and organizes data and information.
- Enterprise resource planning (ERP) systems unites all of a firm’s major departments into a single software program. For instance, production can call up sales information and know immediately how many units must be produced to meet customer orders.
- The client is the application that runs on a personal computer or workstation.
- The server manages network resources or performs special tasks such as storing files, managing one or more printers, or processing database queries.
- An application service provider (ASP) is service company that buys and maintains software on its servers and distributes it through high-speed networks to subscribers for a set period and price.
- Managed service providers (MSPs) are next generation of ASPs, offering customization and expanded capabilities such as business processes and complete management of the network servers.
- Management information systems (MISs) are the methods and equipment that provide information about all aspects of a firm’s operations.
- Management support systems (MSSs) are information systems that use the internal master database to perform high-level analyses that help managers make better decisions.
- A decision support system (DSS) is a management support system that helps managers make decisions using interactive computer models that describe real-world processes.
References
Parts of this chapter are adapted from Chapter 13 of Lawrence J. Gitman, Carl McDaniel, Amit Shah, Monique Reece, Linda Koffel, Bethann Talsma, James C. Hyatt. (2018). Introduction to Business. OpenStax. CC BY 4.0. Access for free at https://openstax.org/books/introduction-business/pages/1-introduction. OpenStax Introduction to Business may be accessed for free at: https://openstax.org/books/introduction-business/pages/1-introduction
Figures
Figure 19.3: Google’s CIO, Ben Fried. Interop Events. 2012. CC BY-NC-ND 2.0. https://flic.kr/p/dgqb3J.
Figure 19.4: Computer networks. Christina Morillo. 2018. Pexels license. https://www.pexels.com/photo/engineer-holding-laptop-1181316/.
Figure 19.5: The iPad Pro is an example of an ultramobile PC. Roberto Nickson. 2019. Unsplash license. https://unsplash.com/photos/hLgYtX0rPgw.
Figure 19.6: Virtual private networks (VPNs). Kindred Grey. 2022. CC BY 4.0. Added command center by Soremba from Noun Project, server by aLf from Noun Project, and computer by Marco Livolsi from Noun Project (Noun Project license). https://archive.org/details/19.5_20220627.
Figure 19.7: Structure of an ASP relationship. Kindred Grey. 2022. CC BY 4.0. Added computer by Marco Livolsi from Noun Project (Noun Project license). https://archive.org/details/19.6_20220627.
Figure 19.8: Example of a company’s integrated information system. Kindred Grey. 2022. CC BY 4.0. https://archive.org/details/19.7_20220627.
Figure 19.9: There’s push to add decision support systems to the clinical field. National Cancer Institute. 2019. Unsplash license. https://unsplash.com/photos/NFvdKIhxYlU.
Figure 19.11: Data security is under constant attack. Tima Miroshnichenko. 2020. Pexels license. https://www.pexels.com/photo/a-computer-monitor-5380589/.
Figure 19.12: How grid and cloud computing work. Kindred Grey. 2022. CC BY 4.0. Added server by aLf from Noun Project, computer by Marco Livolsi from Noun Project, iPad by Mourad Mokrane from Noun Project, Laptop by Saeful Muslim from Noun Project, iPhone by Mr Robot from Noun Project, Earth by Cristiano Zoucas from Noun Project, and person by mim studio from Noun Project (Noun Project license). https://archive.org/details/19.11_202206.
- Home. John Daly. (n.d.). Retrieved from: https://www.dalyinvestment.com/ ↵
- “Innovative Technologies,” TD Ameritrade Institutional, http://www.tdainstitutional.com, accessed February 21, 2018 ↵
- Daly Investment Management website, https://www.dalyinvestment.com, accessed February 21, 2018 ↵
- Daly Investment Management Facebook page, https://www.facebook.com/dalyinvestment, accessed February 21, 2018 ↵
- Jason Compton, “Meet the Supercomputer Driving a Business Boom in the UK,” Forbes, https://www.forbes.com, Junes 14, 2016. ↵
- Patrick Thibodeau, “U.S. To Have 200-Petaflop Supercomputer by Early 2018,” Computer World, https://www.computerworld.com, June 21, 2016. ↵
- Thomas Friedman, The World Is Flat (New York: Farrar, Straus and Giroux, 2005) p. 8. ↵
- Bhavan Jaipragas, “Free Trade for Minnows: How Alibaba Gave Malaysia’s e-Hub Hopes a Boost,” This Week in Asia, http://www.scmp.com, November 20, 2017. ↵
- Asian Companies Count Losses—Hatch Ways to Cope with Weak Dollar,” Reuters, https://www.reuters.com, January 24, 2018 ↵
- Rob Verger, “This Is What Determines the Price of Bitcoin,” Popular Science, https://www.popsci.com, January 22, 2018 ↵
- Bhavan Jaipragas, “Alibaba’s Electronic Trading Hub to Help Small and Medium-sized Enterprises Goes Live in Malaysia,” This Week in Asia, http://www.scmp.com, November 3, 2017 ↵
- Jason Newton and Jesse Gosselin, “VA Looks to Install WiFi after News 8 Story,” WTNH News 8, http://wtnh.com, February 20, 2017. ↵
- “Why Captiva?” https://www.emc.com, accessed February 21, 2018 ↵
- EMC corporate website, “About Us,” https://dellemc.com, accessed February 21, 2018 ↵
- “Lucera Uses Connectivity Routes of Chicago, New York, London and Tokyo as a Trading Hub in Trading Increases,” BSO, https://www.bsonetwork.com, October 19, 2017 ↵
- Ron Miller, “$67 Billion Dell–EMC Deal Closes Today,” Tech Crunch, https://techcrunch.com, September 7, 2016 ↵
- Brian Sherman, “Input Management and Opportunities for the Reseller Channel: An Interview with Wayne Ford, VP of Partner Alliances at Captiva,” ECM Connection, http://www.ecmconnection.com, December 27, 2005 ↵
- Kathryn Balint, “Captiva’s Paper Chase Paying Off,” San Diego Union-Tribune, December 9, 2005, pp. C1, C5. ↵
- Toby Ward, “Technology, the Intranet, and Employee Productivity,” Prescient Digital Media, http://www.prescientdigital.com, accessed February 21, 2018. ↵
- John Quain, “Alexa, What Happened to My Car?” The New York Times, https://www.nytimes.com, January 25, 2018. ↵
- Michael Franco, “The Beginner’s Guide to VPN’s,” Life Hacker, https://lifehacker.com, November 20, 2017. ↵
- NordVPN. (2022, August 3). About Us and our policies. Retrieved from: https://nordvpn.com/about-us ↵
- Chris Preimesberger, “Why Cloud Services Became the New Normal in 2017,” eWeek, http://www.eweek.com, January 4, 2018. ↵
- Bob Evans, “How Cloud Heavyweights Microsoft, Amazon and IBM Will Transform Cloud Computing in 2018,” Forbes, January 3, 2018, https://www.forbes.com. ↵
- “Global Managed IT Service Providers Market 2018-2021,” PR Newswire, https://www.prnewswire.com, January 17, 2018. ↵
- Kathleen Hickey, “Data Warehouses Integrate Supply Chains,” World Trade, February 1, 2006, p. 42. ↵
- Sami Barry, “The Strategic Role of a Chief Knowledge Officer,” Helbling and Associates, Inc. Insights, https://www.helblingsearch.com, September 27, 2012. ↵
- Milon Gupta, “How Strategic Leaders Use Storytelling,” Strategic Thinking, http://www.strategicthinking.eu, November 2, 2015. ↵
- Chris Low, “Information Security Policies Every Business Must Implement,” CIO, https://www.cio.com, August 16, 2017. ↵
- Steve Morgan, “Cyber Crime Costs Projected to Reach $2 Trillion by 2019,” Forbes, https://www.forbes.com, January 17, 2016. ↵
- Sean Michael Kerner, “IDC Analysts Identify IT Security Trends at RSA,” eWeek, http://www.eweek.com, April 22, 2015. ↵
- Ibid. ↵
- Jack Cloherty and Pierre Thomas, “Trojan Horse Bug Lurking in Vital US Computers Since 2011,” ABC News, http://abcnews.go.com, November 6, 2014. ↵
- “Effective Planning and Preparation Can Reduce Impact of 2018 Cyber Security Attacks, Data Breaches,” Yahoo Finance, https://finance.yahoo.com, January 30, 2018. ↵
- Adapted from Tony Bradley, “Top 5 Concerns to Focus on for Privacy Day,” Forbes, https://forbes.com, January 27, 2017. ↵
- Patrick Watson, “Why Bitcoin Has Inflation Risk,” Equities.com, https://www.equities.com, January 13, 2018. ↵
- Kaveh Waddell, “CSI: Walmart,” The Atlantic, https://www.theatlantic.com, April 3, 2017 ↵
- Dave Smith, “Computer Fraud and Abuse Act 2013: New CFAA Draft Aims to Expand, Not Reform, the ‘Worst Law in Technology’,” International Business Times, http://www.ibtimes.com, March 28, 2013 ↵
- “Remote Work is ‘the New Normal,’” Fast Company, https://www.fastcompany.com, February 28, 2018. ↵
- Michael Guta, “3.9 Million Americans—including Freelancers—Now Work from Home at Least Half the Week,” Small Business Trends, https://smallbiztrends.com, April 2, 2018. ↵
- Andrea Loubier, “Benefits of Telecommuting for the Future of Work,” Forbes, https://www.forbes.com, July 20, 2017; Michelle Conlin, “The Easiest Commute of All,” Business Week, December 12, 2005, p. 78. ↵
- Paul Trujillo, “5 Reasons Small Businesses Need the Cloud,” B2C Community, https://www.business2community.com, January 30, 2018. ↵

